For years I’ve used the nslookup utility to quickly confirm that something-or-other about a domain name is correct. Commands like “nslookup -type=soa” roll right off my fingers onto the keyboard not because I’m such a fine typist as because I’ve used them so many times. This has earned me some low-grade derision from Linux-enthusiasts, generally the same types that use vi for everything and cannot comprehend the simple luxury of an application like joe. But I digress. Worse than the personal snootiness is when a shell pops up nonsense like this:
$ nslookup deguia.net Note: nslookup is deprecated and may be removed from future releases. Consider using the `dig' or `host' programs instead. Run nslookup with the `-sil[ent]' option to prevent this message from appearing. Server: 208.201.224.33 Address: 208.201.224.33#53 Name: deguia.net Address: 209.204.175.65
Nslookup is deprecated, use dig. Dig does everything nslookup does, but better and uses five less keystrokes. Well… Yeah, dig will tell me what the A record is for www.deguia.net just fine. It’ll also carry along a screenfull of crap with it:
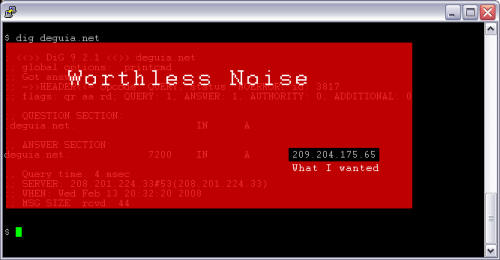
$ dig deguia.net ; <<>> DiG 9.2.1 <<>> deguia.net ;; global options: printcmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 48163 ;; flags: qr aa rd; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 0 ;; QUESTION SECTION: ;deguia.net. IN A ;; ANSWER SECTION: deguia.net. 7200 IN A 209.204.175.65 ;; Query time: 0 msec ;; SERVER: 208.201.224.33#53(208.201.224.33) ;; WHEN: Wed Feb 13 20:39:23 2008 ;; MSG SIZE rcvd: 44
Compare with the simple elegance of nslookup or host:
$ nslookup deguia.net Server: 208.201.224.11 Address: 208.201.224.11#53 Name: deguia.net Address: 209.204.175.65 $ host deguia.net deguia.net has address 209.204.175.65 deguia.net mail is handled by 10 mailin-02.mx.sonic.net. deguia.net mail is handled by 10 mailin-01.mx.sonic.net.
Those two commands together caused less screen-scree than dig did by its little three-letter self. Do I want to wade through all that garbage from dig? Oh hell no. I ran the command to get an answer to a very straightforward question. If I wanted to read a novel I'd have gone to the library. Lots of information there, very little of which is of typically of use to me.
By my calculations, that's roughly a 1:50 signal to noise ratio. For every pixel of output I'm looking for, I'm skimming through 50 pixels of junk. Good old nslookup provides a 1:7 ratio. Same output for my purpose, less jibber jabber, so I waste the five extra keystrokes to save my scroll buffer a little work and keep more previous work on-screen for the moment. More recent versions of host fare well, but lack a crucial ingredient for my purposes: a warning if the response is non-authoritative. That extra couple lines telling where the answer is from has saved my bacon more times than I care to recall.
Earlier today I was perusing lawsofsimplicity.com when a message came through my inbox that reminded me of a little something I'd forgotten all about, the "+short" option. With the +short brewed into a quick little bash alias, dig behaves much more like our good buddy host, but with a lot more handy options available. The web and email content clicked in my head, and I finally find myself willing to give dig another shot.